Today I am working on a sensetive system where administrators share access with third parties and clients. Now we are locking down the system and enabling file auditing. We are interested to know when a file has been deleted or subfolder with files are deleted and who did it! Another issue is someone moves the file somewhere else and this may break a process.
Is this case we are only interested in one folder as it would be insane to monitor the whole computer system, not only would it slow the system down but it would also fill up your event logs fast quick to a point you won’t be able to find what your looking for. OK that say, we still want to monitor this folder and it’s subfolders, the rule here is audit only what you need and select only the audit options nesserary.
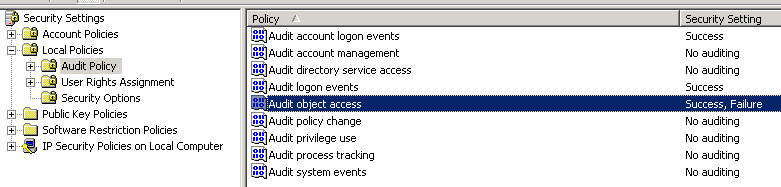
First you need to enable system auditing: Administrator tools> Local Security Setting then local policy> Audit Policy and enable Audit object access for success or failure.
Second go to your folder and Right click selecting sharing and security, select the security tab and click advanced. Now select the Auditing tab and click add, add the group or user to this list and click edit.
To monitor file and deletion or moved files you need to select the following:
- Create Files / Write Data
- Delete Subfolders and Files
- Delete
Click OK and this folder and all subfolders will now be audited.
Testing: (I have removed the following: Date, Time, User, Computer and doamin, but you would expect to see these)
To sucessfully test this create a new text file in the directory, then check the event logs, you are looking for the same Handle and Process ID in this example I have created and renamed the file New Text Document.txt to abc123.txt
Event Type: Success Audit
Event Source: Security
Event Category: Object Access
Event ID: 560
Description:
Object Open:
Object Server: Security
Object Type: File
Object Name: D:\Temp\New Text Document.txt
Handle ID: 1348
Operation ID: {0,173180782}
Process ID: 5928
Image File Name: C:\WINDOWS\explorer.exe
Primary Logon ID: (0x0,0xA1E3C9E)
Client User Name: –
Client Domain: –
Client Logon ID: –
Accesses: READ_CONTROL
SYNCHRONIZE
ReadData (or ListDirectory)
WriteData (or AddFile)
AppendData (or AddSubdirectory or CreatePipeInstance)
ReadEA
WriteEA
ReadAttributes
WriteAttributes
Privileges: –
Restricted Sid Count: 0
Access Mask: 0x12019F
The file has been created and the handle is closed
Event Type: Success Audit
Event Source: Security
Event Category: Object Access
Event ID: 562
Computer: Server01
Description:
Handle Closed:
Object Server: Security
Handle ID: 1348
Process ID: 5928
Image File Name: C:\WINDOWS\explorer.exe
We are now renaming the file and accessing the file to rename it
Event Type: Success Audit
Event Source: Security
Event Category: Object Access
Event ID: 560
Description:
Object Open:
Object Server: Security
Object Type: File
Object Name: D:\Temp\New Text Document.txt
Handle ID: 1348
Operation ID: {0,173181961}
Process ID: 5928
Image File Name: C:\WINDOWS\explorer.exe
Primary Logon ID: (0x0,0xA1E3C9E)
Client User Name: –
Client Domain: –
Client Logon ID: –
Accesses: DELETE
SYNCHRONIZE
ReadAttributes
Privileges: –
Restricted Sid Count: 0
Access Mask: 0x110080
The file New Text Document.txt has been renamed but this appears as delete, If a file is deleted it appears with eventID 564. Here you need to follow the trail of the handle and the process ID.
Event Type: Success Audit
Event Source: Security
Event Category: Object Access
Event ID: 567
Computer: Server01
Description:
Object Access Attempt:
Object Server: Security
Handle ID: 1348
Object Type: File
Process ID: 5928
Image File Name: C:\WINDOWS\explorer.exe
Accesses: DELETE
Access Mask: 0x10000
Now we are accessing the directory to create the file (renamed) notice we have a new handle and process ID
Event Type: Success Audit
Event Source: Security
Event Category: Object Access
Event ID: 560
Description:
Object Open:
Object Server: Security
Object Type: File
Object Name: D:\Temp\abc123.txt
Handle ID: 376
Operation ID: {0,173189724}
Process ID: 9084
Image File Name: C:\WINDOWS\system32\notepad.exe
Primary Logon ID: (0x0,0xA1E3C9E)
Client User Name: –
Client Domain: –
Client Logon ID: –
Accesses: READ_CONTROL
SYNCHRONIZE
ReadData (or ListDirectory)
WriteData (or AddFile)
AppendData (or AddSubdirectory or CreatePipeInstance)
ReadEA
WriteEA
ReadAttributes
WriteAttributes
Privileges: –
Restricted Sid Count: 0
Access Mask: 0x12019F
The file is created
Event Type: Success Audit
Event Source: Security
Event Category: Object Access
Event ID: 567
Description:
Object Access Attempt:
Object Server: Security
Handle ID: 376
Object Type: File
Process ID: 9084
Image File Name: C:\WINDOWS\system32\notepad.exe
Accesses: WriteData (or AddFile)
In this example I did acutally open the file is notepad to write some text. Basically 560 is the file and 567 the action taken.
How to see when a file is deleted: First we see eventID 560 object access, followed by 567 object access attempt and process and then 564 the process which deleted the file.
Event Type: Success Audit
Event Source: Security
Event Category: Object Access
Event ID: 560
Description:
Object Open:
Object Server: Security
Object Type: File
Object Name: D:\Temp\abc123.txt
Handle ID: 1908
Operation ID: {0,173440644}
Process ID: 5928
Image File Name: C:\WINDOWS\explorer.exe
Accesses: DELETE
READ_CONTROL
ReadAttributes
Object Access Request
Event Type: Success Audit
Event Source: Security
Event Category: Object Access
Event ID: 567
Description:
Object Access Attempt:
Object Server: Security
Handle ID: 1908
Object Type: File
Process ID: 5928
Image File Name: C:\WINDOWS\explorer.exe
Accesses: DELETE
The file deleted and the process which performed the delete:
Event Type: Success Audit
Event Source: Security
Event Category: Object Access
Event ID: 564
Description:
Object Deleted:
Object Server: Security
Handle ID: 1908
Process ID: 5928
Image File Name: C:\WINDOWS\explorer.exe
So the rule in this design, is to look out for 560 Events followed by 567 (ADD File, Deleted) and 564 Delete.
I hope you all find this useful. DONT FORGET TO INCREASE YOU EVENT LOG SIZE!